Administrator
Admin



Number of posts : 160
Age : 38
Location : Lucknow
Job/hobbies : Software Engeener
What U like To do ? : Because Its Rock with me.
Registration date : 2008-01-06
 |  Subject: kinds of restrictions implied by the network administrator Subject: kinds of restrictions implied by the network administrator  1/22/2008, 2:06 am 1/22/2008, 2:06 am | |
| - Quote :
there are different kinds of restrictions implied
by the network administrator. One example is restricting access to
certain web sites. This restriction can be bypassed using web proxies.
Another example of restriction generally imposed by the network
administrator is taking away admin rights from the general user. This
can be bypassed using a technique called Privilege escalation. A step
by step tutorial on Privilege escalation is given below for your
reference.
[b]Introduction
Using
the simple command line on a machine running Windows XP, a
non-previleged user can obtain system level privileges, and run the
entire explorer process (Desktop or in other words explorer.exe) . When
done so, all processes that run from it will have system privileges.
The system run level is higher than the administrator, and has full
control of the operating system and it's kernel.
Why this is important?
Local privilege escalation is very useful from an attacker's point of view. The system accont allows for several kernel level
compromises that aren't normally possible (like resetting the administrator password).
What is Local System?
The
Local System account is used by the Windows OS to control various
aspects of the system (kernel, services, etc); the account shows up as
SYSTEM in the Task Manager process list, as seen in the following
screen shot:
 cal cal
System differs from an Administrator account in that it has full
control of the operating system, similar to root on a *nix machine.
Most System processes are required by the operating system, and cannot
be closed, even by an Administrator account; attempting to close them
will result in a error message. The following quote from Wikipedia
explains this in a easy to understand way:
Note:
In
Windows NT and later systems derived from it (Windows 2000, Windows XP,
Windows Server 2003 and Windows Vista), there may or may not be a
superuser. By default, there is a superuser named Administrator,
although it is not an exact analogue of the Unix root superuser
account. Administrator does not have all the privileges of root because
some superuser privileges are assigned to the Local System account in
Windows NT.
Under
normal circumstances, a user cannot run code as System, only the
operating system itself has this ability, but by using the command
line, we will trick Windows into running our desktop as System, along
with all applications that are started from within.
Getting System
We will now walk through the process of obtaining SYSTEM privileges.
To start, lets open up a command prompt (Start > Run > cmd > [ENTER]).
At the prompt, enter the following command, then press [ENTER]:
[/b] [b]at
[/b] If
it responds with an "access denied" error, then we are out of luck,and
you'll have to try another method of privilege escalation; if
itresponds with "There are no entries in the list" (or sometimes
withmultiple entries already in the list) then we are good. Access to
theat command varies, on some installations of Windows, even the
Guestaccount can access it, on others it's limited to
Administratoraccoun ts. If you can use the at command, enter the
following commands,then press [ENTER]:
[b]at 15:25 /interactive "cmd.exe"
[/b] Lets
break down the preceding code. The "at" told the machine to runthe at
command, everything after that are the operators for thecommand, the
important thing here, is to change the time (24 hourformat) to one
minute after the time currently set on your computersclock, for
example: If your computer's clock says it's 4:30pm, convertthis to 24
hour format (16:30) then use 16:31 as the time in thecommand. If you
issue the [b]at command again with no operators, then you should see something similar to this:
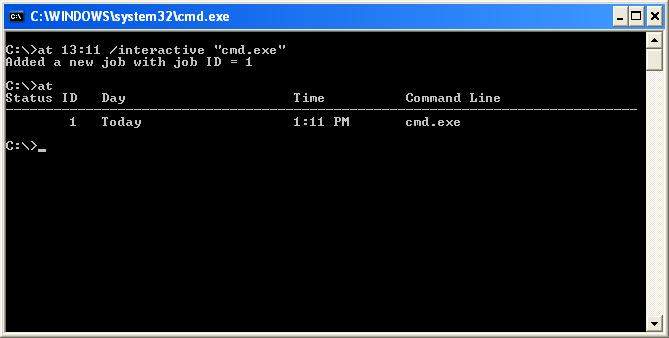
When
the system clock reaches the time you set, then a new command prompt
will magically run. The difference is that this one is running with
system privileges (because it was started by the task scheduler
service, which runs under the Local System account). It should look
like this:
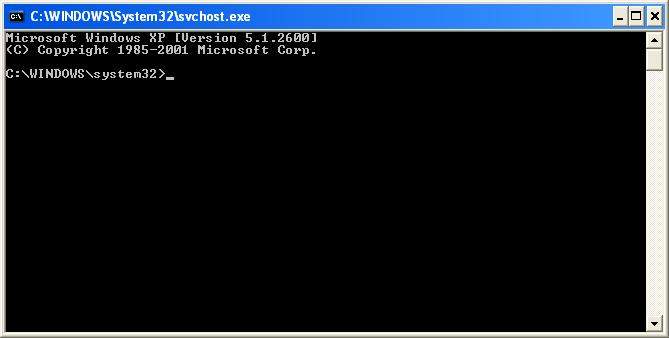
You'll
notice that the title bar has changed from cmd.exe to svchost.exe
(which is short for Service Host). Now that we have our system command
prompt, you may close the old one. Run Task Manager by either pressing
CTRL ALT DELETE or typing taskmgr at the command prompt. In task
manager, go to the processes tab, and kill explorer.exe; your desktop
and all open folders should disappear, but the system command prompt
should still be there.
At the system command prompt, enter in the following:
[/b] [b]explorer.exe
[/b] A
desktop will come back up, but what this? It isn't your desktop. Go to
the start menu and look at the user name, it should say "SYSTEM". Also
open up task manager again, and you'll notice that explorer.exe is now
running as SYSTEM. The easiest way to get back into your own desktop,
is to log out and then log back in. The following 2 screenshots show my
results:


[b]What to do now?
Now
that we have SYSTEM access, everything that we run from our explorer
process will have it too, browsers, games, etc. You also have the
ability to reset the administrators password, and kill other processes
owned by SYSTEM. You can do anything on the machine, the equivalent of
root; You are now God of the Windows machine. I'll leave the rest up to
your imagination.
A quick fix
A
way to prevent this from happening at all, would be to make the task
scheduler service run under a unprivileged account. You can do this by
opening the services control panel (Start > Run > services.msc) ,
and right clicking "Task Scheduler" and going to the Log On tab. Change
it to "This Account" and enter the account information you want it to
use (has to be an existing account) then restart the service. This may
break some programs that use the Task Scheduler and depend on it for
SYSTEM access; you have been warned. Otherwise, simple disable the Task
Scheduler service. [/b] | |
|
